Utilize Cloud Services for Improved Information Protection
In today's digital landscape, the ever-evolving nature of cyber risks demands a positive strategy in the direction of safeguarding delicate data. Leveraging cloud solutions provides a compelling solution for organizations seeking to fortify their data safety measures. By entrusting reliable cloud provider with information administration, businesses can use a wealth of safety features and sophisticated modern technologies that reinforce their defenses versus harmful stars. The question occurs: exactly how can the usage of cloud solutions transform information safety and security techniques and give a robust guard versus possible susceptabilities?
Value of Cloud Security
Ensuring durable cloud security measures is critical in safeguarding sensitive data in today's digital landscape. As organizations progressively count on cloud services to keep and refine their information, the demand for strong security methods can not be overstated. A violation in cloud protection can have extreme effects, ranging from monetary losses to reputational damages.
One of the primary reasons cloud protection is essential is the common responsibility model used by most cloud company. While the provider is in charge of securing the infrastructure, consumers are liable for safeguarding their information within the cloud. This department of obligations underscores the significance of applying durable safety and security measures at the customer level.
Furthermore, with the proliferation of cyber dangers targeting cloud settings, such as ransomware and information violations, organizations should remain aggressive and cautious in mitigating risks. This includes frequently updating safety and security methods, keeping track of for dubious tasks, and educating workers on ideal techniques for cloud safety. By prioritizing cloud safety and security, companies can much better secure their delicate data and support the count on of their stakeholders and consumers.
Information Encryption in the Cloud
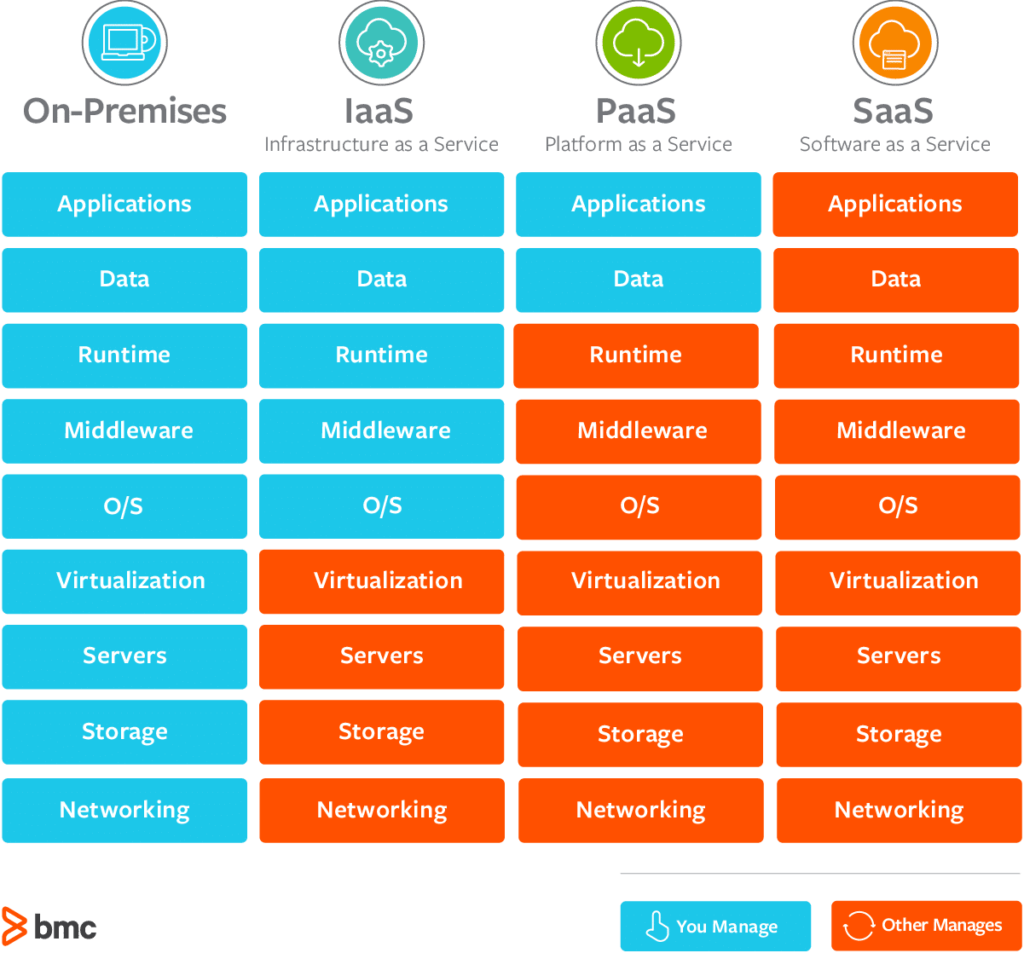
Security in the cloud generally involves the use of cryptographic formulas to clamber data into unreadable formats. Furthermore, lots of cloud service carriers offer security devices to secure data at remainder and in transportation, improving general information security.
Secure Information Back-up Solutions
Data back-up solutions play an essential role in ensuring the strength and safety and security of data in case of unexpected cases or data loss. Secure information backup remedies are important parts of a robust information security method. By frequently backing up information to secure cloud servers, organizations can minimize the risks related to data loss because of cyber-attacks, equipment failures, or human mistake.
Implementing safe and secure information backup remedies involves picking dependable cloud company that provide security, redundancy, and data integrity procedures. Encryption ensures that information stays safe and secure both in transit and at remainder, securing it from unapproved gain access to. Redundancy systems such as home information replication throughout geographically dispersed web servers assist prevent full information loss in situation of web server failings or natural disasters. Additionally, data stability checks guarantee that the backed-up information stays tamper-proof and unchanged.
Organizations must establish computerized back-up schedules to guarantee that data is constantly and effectively backed up without hand-operated treatment. When required, normal testing of data reconstruction procedures is also important to guarantee the performance of the back-up options in recuperating information. By purchasing safe and secure information backup services, services can enhance their data safety and security pose and minimize the influence of possible information violations or disturbances.
Duty of Access Controls
Applying strict access controls is critical for maintaining the safety and stability of sensitive info within business systems. Accessibility controls function as a critical layer of defense versus unapproved access, making certain that just accredited individuals can check out or adjust delicate data. By specifying that can access particular sources, organizations can limit the threat of data breaches and unapproved disclosures.

Regularly updating and examining accessibility controls is important to adapt to organizational adjustments and progressing safety threats. Constant tracking and bookkeeping of accessibility logs can aid find any kind of suspicious tasks and unauthorized accessibility efforts without delay. On the whole, robust access controls are fundamental in guarding sensitive information and mitigating safety and security risks within organizational systems.
Compliance and Laws
On a regular basis ensuring conformity with relevant regulations and requirements is essential for companies to promote information security and privacy measures. In the world of cloud services, where information is typically saved and processed externally, adherence to industry-specific guidelines such as GDPR, HIPAA, or PCI DSS is crucial. These policies mandate certain data dealing with techniques to secure delicate details and make certain individual personal privacy. Failure to follow these laws can cause extreme fines, consisting of penalties and legal activities, harming a company's online reputation and count on.
Many companies offer file check this site out encryption abilities, gain access to controls, and audit routes to help companies fulfill data safety and security requirements. By leveraging certified cloud solutions, organizations can enhance their information security stance while satisfying governing responsibilities.
Verdict
To conclude, leveraging cloud solutions for boosted information safety is important for organizations to protect delicate info from unapproved accessibility and possible violations. By applying robust cloud safety methods, including information file encryption, safe backup solutions, gain access to controls, and conformity with policies, services can take advantage of sophisticated protection steps and expertise used by cloud company. This assists reduce threats successfully and ensures the confidentiality, honesty, and accessibility of information.

Information backup solutions play an important function in guaranteeing the strength and safety and security of information in the occasion of unanticipated events or data loss. By frequently backing up information to safeguard cloud web servers, organizations can alleviate the dangers associated with information loss due to cyber-attacks, equipment failures, or human error.
Applying protected data backup remedies involves selecting reputable cloud service suppliers that use encryption, redundancy, and information integrity steps. By spending in secure information backup options, businesses can improve their data protection pose and lessen the impact of prospective information violations or interruptions.